Most CPA firms understand they need a Written Information Security Plan, commonly called a WISP.
However, many firms are unclear about what actually needs to be inside it. More importantly, they often do not know what regulators and insurance carriers expect to see during a review.
This guide outlines the most important CPA WISP requirements under the IRS Safeguards Rule and explains what documentation CPA firms should maintain to stay compliant.
Core WISP Deliverables Every CPA Firm Should Include
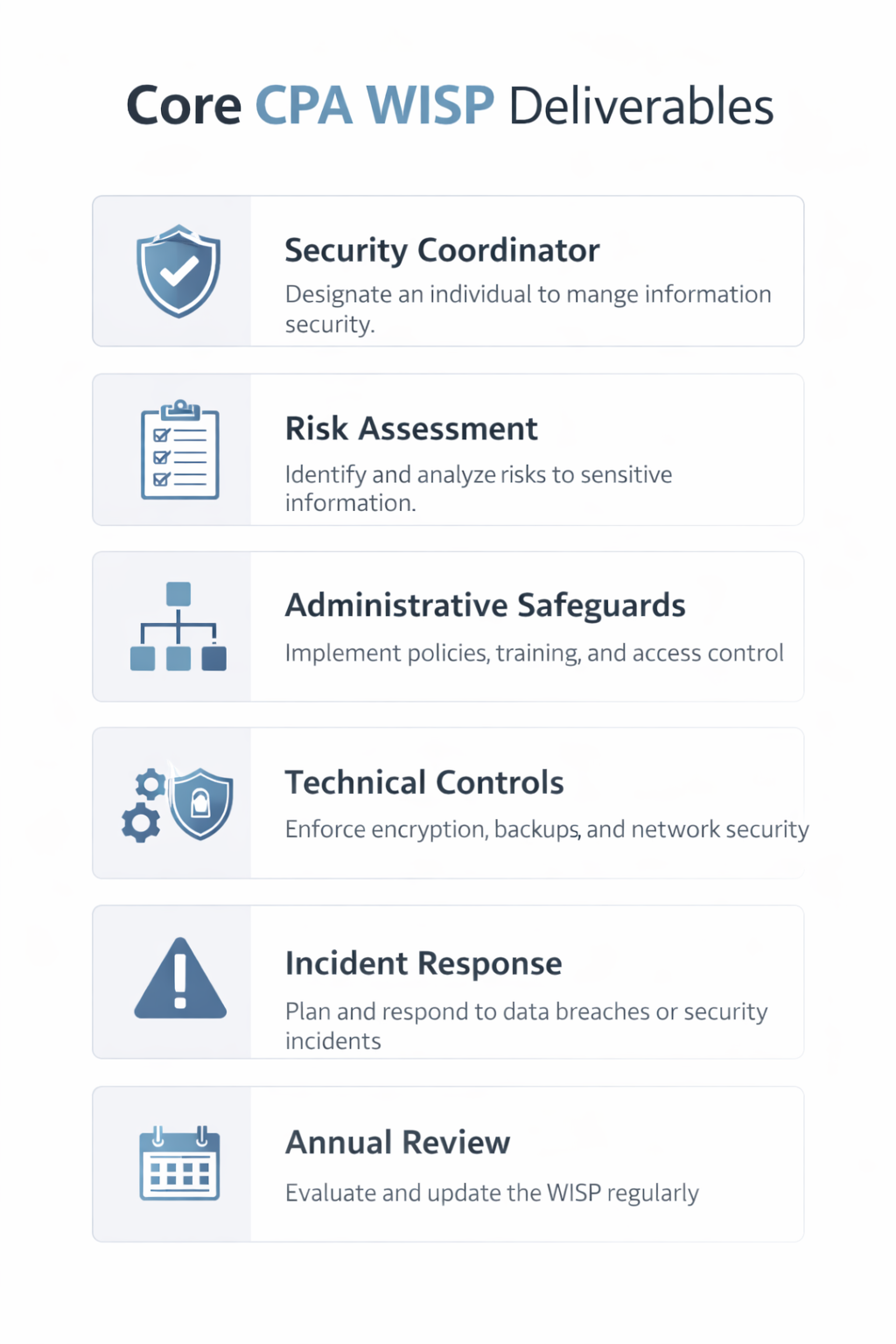
A strong Written Information Security Plan reflects how your firm actually operates. The following components form the foundation of defensible compliance.
1. Designated Security Coordinator
Your documentation must clearly identify who is responsible for data protection oversight and compliance management. For smaller firms, this often involves leadership working alongside an MSP specializing in accounting firms.
2. Documented Risk Assessment
A compliant WISP includes written risk identification, impact evaluation, and mitigation strategy mapping. Simply listing antivirus software is not enough.
Risk Assessment Must Align With Controls

Effective CPA WISP requirements go beyond listing risks. Your documentation should clearly connect each identified threat to an implemented safeguard.
For example, phishing risk should map directly to multi factor authentication, email filtering, and employee training policies.
If you have already reviewed our guide on IRS IT security requirements for CPA firms, you understand that layered controls must support documented policies.
Incident Response Planning

Every CPA firm must document how incidents are detected, escalated, contained, and reported. An incident response plan is not optional under IRS Safeguards expectations.
- Defined internal notification process
- Client notification framework
- Documentation procedures
- Post-incident remediation tracking
Without a structured response plan, even minor security events can create regulatory exposure.
Ongoing Review and Annual Maintenance

A Written Information Security Plan must evolve as your firm changes. Annual reviews ensure documentation reflects real infrastructure, staffing, and workflow adjustments.
- Annual risk reassessment
- Control validation
- Documentation updates
- Version tracking
If your documentation has not been reviewed in the past 12 months, it likely no longer reflects your current environment.
Where CPA Firms Commonly Fall Short
Across compliance reviews, we consistently observe three recurring gaps:
- Generic templates that do not reflect firm operations
- Controls implemented but not documented
- Policies that do not match technical infrastructure
Alignment between documentation and reality determines defensibility.
Next Step: A Practical CPA Compliance Review
If you are unsure whether your current WISP would withstand regulatory scrutiny or insurance review, clarity is the next step.
We offer a CPA focused compliance assessment that evaluates documentation alignment, identifies risk gaps, and provides a prioritized roadmap.
Schedule a CPA Compliance Review
Frequently Asked Questions
What are the minimum CPA WISP requirements?
At minimum, CPA firms must document a security coordinator, risk assessment, administrative safeguards, technical controls, incident response plan, and annual review process under IRS Safeguards expectations.
Do small CPA firms need a Written Information Security Plan?
Yes. IRS Safeguards requirements apply regardless of firm size if the firm handles Federal Tax Information.
How often should a CPA firm review its WISP?
CPA firms should review and update their WISP annually or whenever significant operational or technology changes occur.
Can a CPA firm use a generic WISP template?
Templates can provide a starting point, but they rarely reflect firm specific risk exposure or infrastructure alignment. Documentation must match actual safeguards.

